He is an experienced SEO Specialist and content writer with a passion for driving online visibility and engagement. With years of experience in the digital...Read more
|
Getting your Trinity Audio player ready...
|
Hey there! Have you ever heard about hacking assaults? They’re like sneaky burglars trying to interrupt your computer and steal your stuff!
But do not worry—there’s something called an antivirus that acts like a superhero to defend your computer from hacking attacks.
It’s like a defense that protects your computer from horrific guys lurking on the net. Imagine being capable of using your PC with no issues, knowing that it’s safe from hackers.
Wouldn’t that be superb? Well, this is exactly what an antivirus software program does! It offers you peace of mind and helps you browse the internet, play video games, and do homework without fear of cyberattacks.
So, the next time you operate your laptop, remember the significance of antivirus software in keeping it safe from hacking attacks.
It’s like having a digital bodyguard that maintains your private information and documents secure. Keep your laptop protected and stay safe online with antivirus software!
Table of Contents
Understanding Hackers and Cyber Threats
They come in numerous forms, from script kiddies searching for a reputation to state-of-the-art, nation-subsidized cybercriminals aiming for strategic advantage.
Cyber threats faced by people and organizations vary from phishing scams and malware assaults to ransomware incidents that may cripple entire structures.
These threats make the most vulnerabilities in software or human behavior to infiltrate networks, thieve touchy records, or disrupt operations.
Understanding hackers’ reasons is essential in comprehending the ever-evolving landscape of cybersecurity.
People and groups can better protect themselves despite ability breaches and financial losses by knowing about their processes and techniques.
Who are hackers?

Hackers are individuals with a diverse set of talents and motivations. They can range from curious fans exploring vulnerabilities to malicious actors searching for monetary gain or political reasons.
These individuals have the technical prowess to exploit weaknesses in structures, networks, and software programs.
Some hackers function independently, while others may be a part of organized crime organizations or nation-subsidized entities.
The anonymity furnished with the aid of the digital international permits hackers to conceal their identities and places, making it difficult for law enforcement corporations to song them down.
Common cyber threats faced by individuals and corporations
Cyber threats loom big within the digital panorama, posing dangers to people and agencies.
One unusual danger is phishing, wherein hackers use misleading emails or messages to trick recipients into divulging touchy information like login credentials or economic info.
Stay vigilant and informed about these cyber threats as they persevere to conform and adapt to today’s interconnected global.
Can Antivirus Stop Hackers?
Hackers are professionals who continuously look for system vulnerabilities to make the most of their benefit.
They use phishing, malware, and ransomware to infiltrate networks or scouse and borrow sensitive information.
Antivirus software programs perform a crucial function in detecting and blocking those malicious threats earlier than they can harm purposely.
However, it’s vital to recognize that antivirus programs have boundaries and may not be capable of forestalling all hacking attempts.
While antivirus can successfully locate known malware signatures and suspicious behavior styles, hackers are constantly evolving their tactics to skip those safety features.
This highlights the need for a multi-layered approach to cybersecurity, incorporating firewalls, intrusion detection structures, and everyday software updates.
Despite the effectiveness of antivirus software programs in stopping many hacking attacks, people and businesses must implement additional security measures, such as robust passwords, statistics encryption, employee education on cybersecurity practices, and normal backups of critical files by combining antivirus safety with proactive safety features.
Limitations of antivirus software program

Antivirus software, while crucial in protecting against regarded threats, does have its limitations. One of the main demanding situations is that conventional antivirus applications rely upon signature-primarily based detection strategies.
With this approach, they can only identify malware that matches a pre-present database of regarded signatures. As hackers continuously broaden new and complicated techniques, zero-day assaults and polymorphic malware can effortlessly pass these static defenses.
Moreover, antivirus software may additionally use warfare to locate positive forms of advanced persistent threats (APTs) or file-less malware that operates stealthily within a machine’s memory without leaving traces on a disk in which most antivirus tools normally experiment for threats.
Additionally, a few hackers use encryption or obfuscation strategies to avoid detection through antivirus packages, making it even more difficult for them to block these malicious spots efficiently.
Furthermore, as cybercriminals evolve their processes and shift towards social engineering assaults or phishing schemes to trick users into unknowingly putting in malware, relying entirely on antivirus protection may not be sufficient.
Individuals and corporations must complement their security features with other proactive strategies, such as relying on an antivirus software program on their own.
How antivirus detects and prevents hacking attempts
Antivirus software operates like a vigilant virtual defense, continuously scanning your device for any signs of malicious hobby. It works by comparing files to acknowledged malware signatures to stumble on threats.
When it identifies suspicious conduct or code styles, the antivirus triggers an alert and takes movement to neutralize the chance.
Moreover, cutting-edge antivirus packages use heuristic analysis to identify new varieties of malware based on behavioral patterns instead of just specific signatures. This proactive method allows them to block potentially dangerous actions before they can cause harm.
Additionally, a few antiviruses offer actual-time safety features that constantly display your gadget for any unusual sports. These tools are designed to forestall hacking tries in their tracks, efficiently preventing unauthorized rights of entry and records from being breached.
Antivirus software is crucial in safeguarding your devices from diverse hacking attempts. It stays up-to-date with modern safety patches and often updates virus definitions.
Understanding the unique kinds of hacking attacks
Hacking attacks come in diverse forms, each with its processes and objectives. One common kind is malware, which incorporates viruses, worms, and ransomware designed to infiltrate neglected systems.
Social engineering exploits human psychology to govern individuals by divulging private facts or granting the right of entry to steady structures.
SQL injection attacks target databases by inserting malicious code to retrieve sensitive information. Man-in-the-middle assaults intercept conversations between two parties without their expertise.
Understanding these numerous hacking techniques is essential for enforcing robust cybersecurity measures beyond relying completely on antivirus software programs.
Strengthening Cybersecurity Beyond Antivirus
In a trendy virtual panorama, depending entirely on antivirus software isn’t always enough to safeguard against state-of-the-art cyber threats. To improve cybersecurity beyond antivirus, adopting a multi-layered protection approach is important.
This includes enforcing firewalls, intrusion detection systems, and normal device and software protection updates.
Educating personnel about cybersecurity best practices and conducting everyday schooling sessions can extensively improve common protection against hacking attempts. Additionally, encrypting sensitive information at rest and in transit provides protection against potential breaches.
Regularly monitoring community visitors for uncommon sports or anomalies can help locate ability threats early on. Implementing sturdy password policies and allowing –issue authentication further fortifies individuals’ and corporations’ security posture.
By incorporating these additional measures and antivirus safety, companies can create a sturdy protection mechanism that greatly reduces the danger of falling victim to cyber-attacks.
Importance of adopting a multi-layered protection method
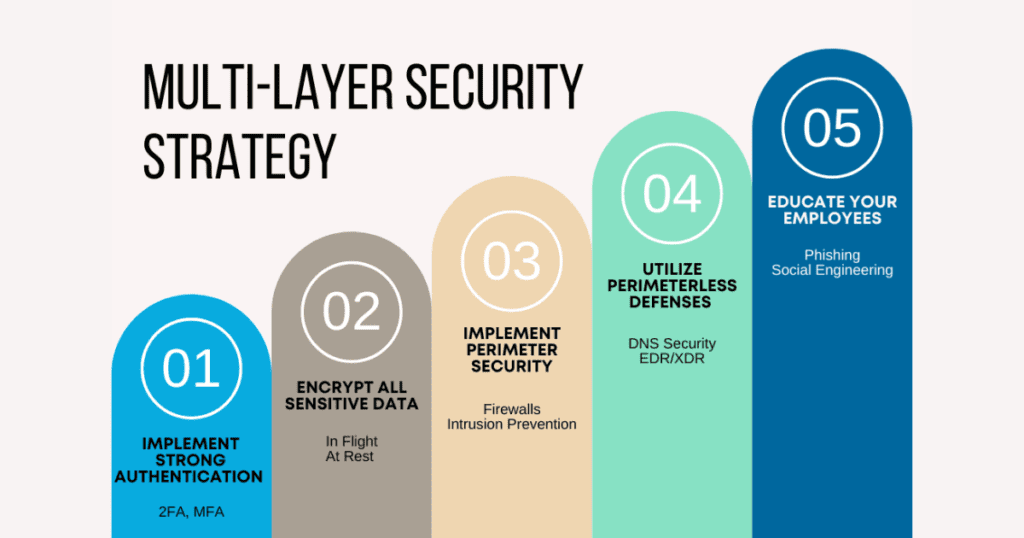
In the ever-evolving digital landscape, guarding against hackers requires more than relying completely on antivirus software applications.
Hackers have emerged as an increasing number of modern-day in their tactics, making it crucial for people and agencies to undertake a multi-layered safety method.
A multi-layered protection strategy includes implementing diverse protection mechanisms throughout special degrees of your community infrastructure.
This should encompass firewalls, intrusion detection systems, encryption protocols, and everyday protection audits.
By diversifying your cybersecurity measures, you create some limitations hackers should overcome to breach your system efficiently.
This makes it substantially tougher for them to infiltrate and compromise touchy information or structures within your network.
While antivirus software programs are crucial in detecting recognized threats, combining them with superior safety technology complements protection against emerging cyber threats.
Remember, the more layers of defense you have in place, the better geared you are to thwart capability hacking assaults and shield your digital belongings.
Additional measures to protect against hackers
Implementing additional safety features in addition to antivirus software programs is important in protecting against hackers. One effective approach is regularly replacing software and operating systems to patch vulnerabilities that hackers could exploit.
Utilizing sturdy, unique passwords for debts can also improve cybersecurity by making it harder for hackers to guess or crack passwords.
Implementing two-issue authentication adds a further layer of security by requiring a second verification form before accessing debts.
Educating personnel on cybersecurity-friendly practices through schooling classes can help prevent social engineering attacks like phishing.
Encouraging vigilance while clicking links or downloading attachments from unknown resources can save you from malware infections.
Regularly backing up domestic and offsite records ensures that vital data stays steady, even if hackers compromise structures.
Encrypting sensitive records provides another level of safety, making it more difficult for unauthorized customers to access treasured statistics.
A robust firewall can help monitor incoming and outgoing community site visitors, blockading capability threats before they attain the device.
Conducting normal protection audits and tests enables picking out weaknesses within the cybersecurity posture and permit timely remediation actions.
By combining those extra security features with antivirus software, people and companies can strengthen their protection against hacking attacks.
The effectiveness of antivirus in preventing these attacks
Antivirus software programs are powerful in stopping known threats by scanning documents and tracking device sports for suspicious conduct, but they have boundaries.
Supplementing antivirus safety with other security features, including firewalls, intrusion detection structures, normal software program updates, robust passwords, and worker education on exceptional cybersecurity practices is essential.
Adopting a multi-layered security technique and staying vigilant against rising threats could improve your universal cybersecurity posture and decrease the risk of being hacked.
Real-world examples of successful hacking attacks, not with standing having antivirus software
In the ever-evolving panorama of cybersecurity, regardless of antivirus software in the region, hackers have determined ways to skip these defenses and execute successful hacking assaults.
One first-rate instance is the WannaCry ransomware attack, which targeted companies and groups internationally, regardless of whether many had antivirus protection installed on their systems.
This malicious software exploited a vulnerability in previous Windows structures, spreading rapidly and encrypting files till a ransom was paid.
The impact was full-size, inflicting disruptions throughout diverse sectors and highlighting the need for continuous security updates beyond relying on antivirus programs.
Similarly, state-of-the-art phishing attacks have tricked customers into clicking malicious hyperlinks or supplying sensitive records directly to hackers.
These social engineering processes can avoid conventional antivirus detection techniques, emphasizing the significance of person recognition schooling alongside strong cybersecurity measures.
As cyber threats keep evolving, individuals and groups must remain vigilant against capability vulnerabilities that cannot be completely mitigated with antivirus alone.
Limitations and vulnerabilities of antivirus applications

While antivirus packages play an important function in shielding gadgets from malware and viruses, they may need to be more foolproof.
One difficulty is that conventional signature-primarily based antivirus software can also conflict with detecting new or evolving threats that still need to be identified and delivered to their databases.
This leaves systems liable to zero-day attacks in which hackers exploit previously unknown vulnerabilities.
Moreover, some state-of-the-art hacking strategies, like file-less malware, can pass traditional antivirus detection strategies by running at once inside the computer’s memory without leaving lines under tough pressure.
Additionally, attackers can use social engineering methods to trick customers into unknowingly disabling or uninstalling antivirus programs.
Furthermore, as cyber threats become more complicated and numerous, customers must understand that relying completely on antivirus software won’t offer complete protection against all hacking assaults.
Complementing antivirus solutions with additional security measures, such as regular updates, robust passwords, and network firewalls, reinforces standard cybersecurity posture.
Additional security measures to complement antivirus protection
In the modern, ever-evolving cyber threat landscape, depending solely on antivirus software programs won’t be sufficient to shield your gadgets and records completely. To bolster your cybersecurity defenses, remember to enforce additional security measures that complement your antivirus protection.
One powerful approach is often updating all software programs and working structures on your devices. Software updates frequently encompass patches for recognized vulnerabilities hackers may want to explore.
Another important step is educating yourself and your crew about cybersecurity quality practices. By focusing on phishing scams, social engineering tactics, and other common threats, you can empower everyone to be vigilant against ability assaults.
Furthermore, using strong passwords and implementing multi-component authentication adds a layer of safety to save you from unauthorized entry to accounts and touchy information.
Encrypting sensitive information at rest and in transit can also help shield cybercriminals from intercepting or compromising it.
Additionally, installing firewalls and intrusion detection systems gives you a normal protection posture against hacking attempts.
Conclusion
The landscape of cybersecurity is ever-evolving and complex. Robust defense mechanisms are paramount, from state-of-the-art hacking attacks to continuously mutating threats.
While antivirus software programs play an important function in safeguarding against acknowledged malware and viruses, it’s crucial to apprehend their obstacles.
A multi-layered protection technique that combines antivirus with firewalls, intrusion detection systems, ordinary software program updates, worker education on cybersecurity best practices, and strong password policies can notably improve protection against hackers.
Read More About: Anti Virus

He is an experienced SEO Specialist and content writer with a passion for driving online visibility and engagement. With years of experience in the digital marketing.
- Latest Posts by Shaheer Akram
-
What is the new virus going around?
- -
Can Chromebooks get viruses?
- -
How to Check Your Phone for Viruses?
- All Posts

